Amplitude Shift Keying (ASK) Demodulation
Amplitude Shift Keying (ASK) is a fundamental modulation scheme in digital communication systems. It encodes binary data by varying the amplitude of a carrier signal. Due to its simplicity and cost-effectiveness, ASK is widely used in low-power and bandwidth-constrained applications such as RFID systems, optical communications, and telemetry. However, the process does not end at modulation; the receiver must extract the original binary data from the modulated signal through a process called demodulation. In this blog, we explore the two main techniques for ASK demodulation, namely Asynchronous ASK Demodulation and Synchronous ASK Demodulation, diving into their principles, workflows, advantages, and mathematical foundations.
What is ASK Demodulation?
ASK demodulation refers to the process of retrieving the original binary data encoded in the amplitude variations of a carrier signal. It is a crucial step in communication systems to recover information from the transmitted signal. The choice of demodulation technique depends on system requirements such as complexity, cost, and robustness to noise.
The two main types of ASK demodulation are:
- Asynchronous ASK Demodulation: A simple method that does not require synchronization with the carrier.
- Synchronous ASK Demodulation: A robust approach that relies on synchronized detection.
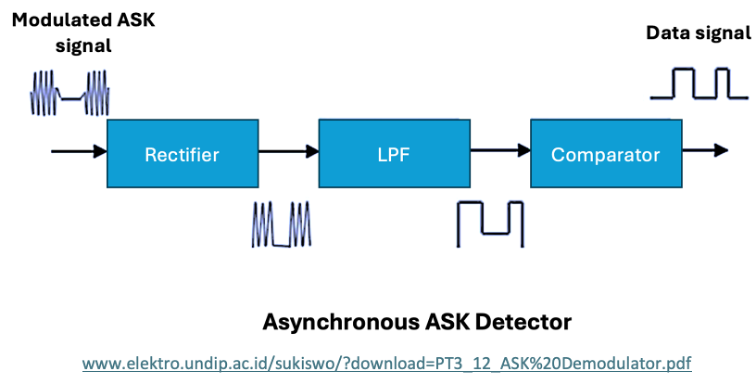
Asynchronous ASK Demodulation
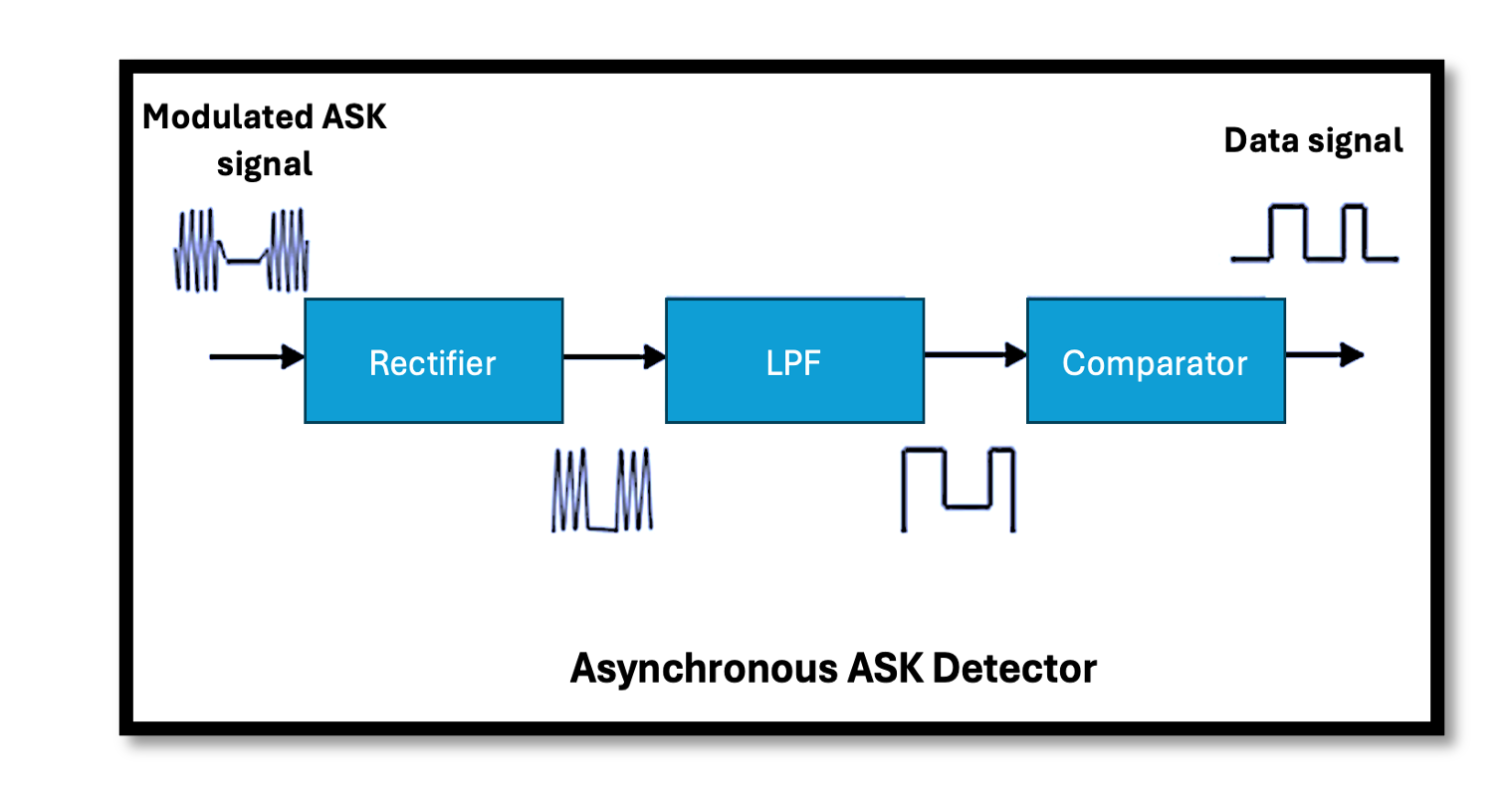
Asynchronous demodulation is a straightforward method that extracts binary data without relying on synchronization with the carrier signal. This makes it simple and cost-effective but less robust in noisy environments.
Key Components and Workflow
- Rectifier:
- The rectifier processes the incoming modulated ASK signal and converts it into a unipolar signal.
- By removing the negative portions of the signal, the rectifier ensures the envelope (representing the amplitude variations) is preserved.
- Output: A unipolar version of the original ASK signal with peaks corresponding to the amplitude variations.
- Low-Pass Filter:
- The rectified signal is then passed through a low-pass filter to smooth out high-frequency components, retaining only the envelope of the signal.
- The filtered output corresponds to the baseband signal, which directly represents the amplitude changes encoding the binary data.
- Output: A continuous waveform representing binary 1 and 0 as high and low amplitude regions.
- Comparator:
- The comparator compares the low-pass filtered signal against a predefined threshold voltage.
- If the signal amplitude exceeds the threshold, it is interpreted as a binary 1; otherwise, it is interpreted as a binary 0.
- Output: A digital signal comprising a sequence of binary 1s and 0s.
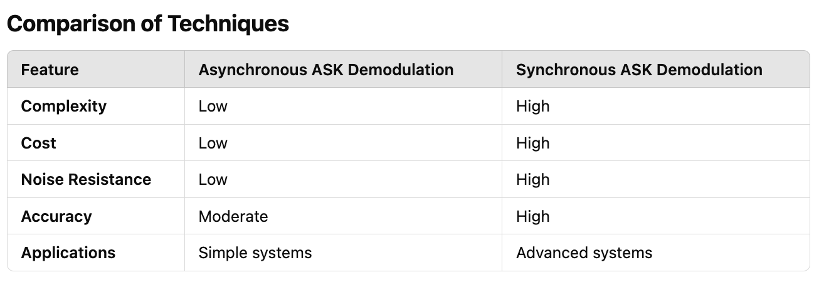
Advantages of Asynchronous ASK Demodulation
- Simplicity: The circuit is easy to design and implement.
- Cost-Effectiveness: Requires minimal components, making it ideal for low-budget systems.
- Ease of Use: Does not need carrier synchronization, simplifying operation.
Limitations
- Noise Susceptibility: Without synchronization, the method is more prone to errors in the presence of noise.
- Threshold Sensitivity: Accurate tuning of the threshold voltage is critical to ensure proper binary classification.
Synchronous ASK Demodulation
Synchronous demodulation is a more advanced and robust method that relies on precise synchronization with the carrier signal. By using synchronization, it offers higher accuracy in extracting binary data, even in noisy environments.
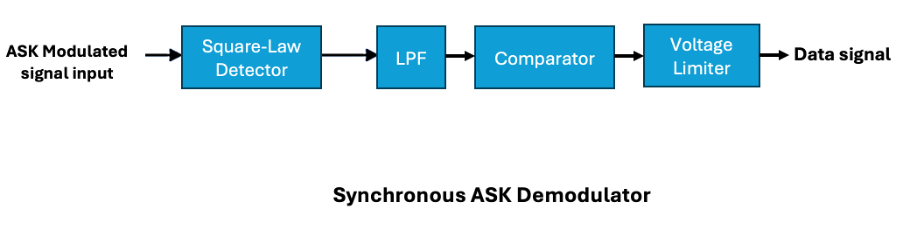
Key Components and Workflow
- Square-Law Detector:
- The incoming modulated ASK signal is processed by a square-law detector. This component squares the amplitude of the signal to amplify the differences between the binary states (1 and 0).
- The mathematical operation produces a signal with both high-frequency (2ωc) and low-frequency (DC) components.
The output of the square-law detector is:
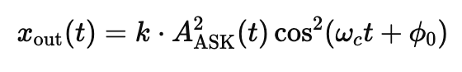
Here, AASK(t) is the signal amplitude, ωc is the carrier frequency, and ϕ0 is the phase. This equation can be expanded into:
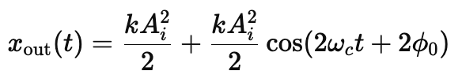
Where (kAi2/2) is the low-frequency DC term, and the high-frequency term (cos(2ωct+2ϕ0)) is removed in the subsequent filtering stage.
2. Low-Pass Filter:
- The squared signal is passed through a low-pass filter to remove the high-frequency components (2ωc) while retaining the DC term.
- xthreshold = kAi2/2
- This component corresponds to the squared amplitude of the carrier signal for binary 1 or 0.
3. Comparator:
- The filtered signal is compared against a threshold value using a comparator.
- If xthreshold = Threshold, the signal is identified as binary 1 (high amplitude). Otherwise, it is classified as binary 0 (low amplitude).
4. Voltage Limiter:
- The comparator output is passed through a voltage limiter to standardize the binary signal into voltage levels such as 0V for binary 0 and 2V for binary 1.
The block diagram summarises this process:
- The ASK modulated input is first squared, resulting in high and low-frequency components.
- The low-pass filter isolates the DC component (kAi2/2).
- The comparator detects whether the amplitude represents a 1 or 0, based on a threshold.
- Finally, the voltage limiter adjusts the binary signal to a standard output voltage level.
This method ensures high accuracy and robustness against noise, making it ideal for systems requiring reliable data recovery.
Advantages of Synchronous ASK Demodulation
- High Accuracy: Synchronization with the carrier ensures reliable detection of binary states.
- Noise Resistance: Less prone to noise and fading compared to asynchronous methods.
- Robustness: Ideal for complex systems operating in noisy environments.
Limitations
- Complexity: Requires synchronization circuitry, increasing design complexity.
- Cost: Higher component requirements make it more expensive than asynchronous demodulation.
Mathematical Analysis
Asynchronous Demodulation:
- The output relies on amplitude comparisons with a threshold. If A>Vthreshold, the signal is classified as 1, otherwise 0.
Synchronous Demodulation:
- The squared output contains a dominant DC component after filtering:
xthreshold = kAi2/2
where Ai corresponds to the amplitude levels. The comparator distinguishes binary 1 (high amplitude) and 0 (low amplitude) based on this value.
Applications of ASK Demodulation
- RFID Systems:
- ASK modulation and demodulation are commonly used in RFID tags and readers for efficient data communication.
- Infrared Communications:
- Consumer electronics such as remote controls use ASK demodulation for transmitting commands over infrared signals.
- Telemetry Systems:
- ASK is employed in telemetry systems to send sensor data in low-power and bandwidth-limited applications.
- Optical Communications:
- ASK demodulation is used in fiber-optic communication systems for its simplicity and cost-effectiveness.
Take our entry level course (Below) for free using coupon code RAHRF101BLOG
RF Fundamentals, Basic Concepts and Components – RAHRF101
For limited time take an additional 10% off of all our courses using coupon code RFCERT10
Rahsoft RF Certificate and courses
Conclusion
ASK demodulation is a cornerstone of digital communication, enabling the retrieval of binary data from amplitude-modulated signals. The choice between asynchronous and synchronous methods depends on the application’s requirements for complexity, cost, and noise resistance. While asynchronous demodulation is suitable for simple and cost-sensitive applications, synchronous demodulation is preferred for high-precision systems operating in noisy environments. By understanding the principles and workflows of these methods, engineers can design efficient and reliable communication systems tailored to specific needs. Whether in RFID systems, infrared controls, or optical communications, ASK demodulation continues to play a vital role in modern technology.

Learn more about this topic by taking the complete course ‘Introduction to Modulation in Communication Systems Online Course – RAHRF152’. Watch the course videos for more detailed understanding. Also checkout other courses on RF system and IC design on https://rahsoft.com/courses/. Rahsoft also provides a certificate on Radio Frequency. All the courses offer step by step approach.